The contents of the zip are as follows:
Timeline Report.EnPack
Timeline Report.EnScript (actual code)
Timeline_Report_README.pdf
Timeline_Report_WHATSNEW.pdf
Include\GNB_HTMLlib.EnScript (library file)
Include\GNB_XMLlib.EnScript (library file)
I must say that it's nice that Geoff has given us the code to his Timeline script so that one can modify as desired. It's also nice that he includes README and WHATSNEW files so you can have something to reference for past and present versions.
Simply unzip these items (without the pdfs) into your EnCaseX\EnScript folder and you are ready to go. You can run the script by either double clicking the EnPack or the EnScript, just make sure to add a disk image to the case first ;-). When you run it you will see the following:

There are a lot of options you can choose. Here's a closeup of the interface itself:
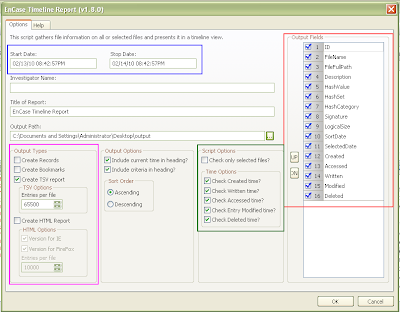
You can pick a certain time period with a start and stop date for the timeline (boxed in blue). You can pick the type of output you want (boxed in pink), whether you want Records, Bookmarks, a Tab Delimited report (TSV), how many entries you'd like in each TSV file and whether or not you would like an HTML report better suited for IE or Firefox. There are more Script Options and Time Options (boxed in green) that allow you to select files you want in the timeline report (default is all files) and which time entries you are interested in seeing (default is all). You can modify the order to the Output Fields (boxed in red) for the TSV file or remove fields that are not of interest. Other fields are self explanatory.
While the script is running you can see the progress bar at the bottom right. If you choose the HTML report option you may end up with several HTML files (depending on how many files are selected and how many entries per file you have selected) and if this is the case each file is named in order for example:
TimelineReport-FF.html
TimelineReport-FF2.html
TimelineReport-FF3.html
and so on... You can see an example report below:

The latest change is highlighted, but you can see that some files might have the same time stamp for different fields. In this case the file will be listed twice, once with Created highlighted and once with Accessed highlighted (from the README).
You can check out some of Geoff's other EnScripts and CEIC presentations at his website: http://www.geoffblack.com/forensics.